Popular x64 Tags
- software x64 download
- network x64 download
- download x64 download
- seo x64 download
- online tv x64 download
- rss reader x64 download
- internet x64 download
- freeware x64 download
- free x64 download
- identity management x64 download
- hardware inventory x64 download
- slow pc performance x64 download
- utility x64 download
- proxy x64 download
- satellite tv for pc x64 download
- email x64 download
- password manager x64 download
- password reset x64 download
- security x64 download
- address x64 download
- server x64 download
- web x64 download
- remote control software x64 download
- pages x64 download
- rss x64 download
- password management x64 download
- active directory x64 download
- why is my computer so slow x64 download
- software distribution x64 download
- software inventory x64 download
I2P 2.11.0
Sponsored links:
license: Freeware
downloads: 470
size: 23.90 MB
updated: 2026-02-10
tags: I2P, download I2P, I2P free download, network message, network communication, tunnel manager, network, message, peer, stream
Add to Basket
I2P Team
**I2P: The Invisible Internet Project - A Comprehensive Review**
The Invisible Internet Project, commonly known as I2P, is a robust and sophisticated software solution developed by the I2P Team. It is designed to provide users with a secure and anonymous communication network, ensuring privacy and freedom from surveillance.
### Overview
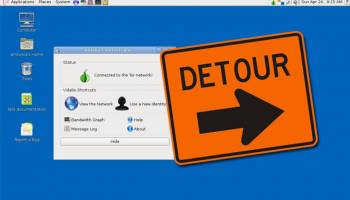
I2P is an open-source project that focuses on creating a decentralized and anonymous overlay network. This network allows applications to send messages to each other securely and anonymously. Unlike traditional internet protocols, I2P is built to operate within its own network, providing a layer of privacy that is difficult to penetrate.
### Key Features
1. **Anonymity**: I2P excels in providing anonymity for both the sender and receiver. It achieves this through a complex routing mechanism known as garlic routing, which encrypts multiple messages together to obfuscate the data.
2. **Decentralization**: The network is decentralized, meaning there is no central authority or server that can be targeted for attacks. This makes I2P highly resilient against censorship and surveillance.
3. **Versatile Applications**: I2P supports a wide range of applications including web browsing, email, file sharing, and instant messaging. It is compatible with various protocols and can be integrated with existing applications to enhance their privacy features.
4. **End-to-End Encryption**: All communications within the I2P network are end-to-end encrypted, ensuring that data remains confidential and tamper-proof during transit.
5. **Community-Driven**: Being an open-source project, I2P benefits from a vibrant community of developers and users who continuously contribute to its improvement and security.
### Performance
I2P is designed to be efficient and scalable. It can handle a large number of users and high traffic volumes without significant degradation in performance. The software is lightweight and can run on various operating systems including Windows, macOS, Linux, and Android.
### Usability
While I2P offers advanced privacy features, it is also user-friendly. The installation process is straightforward, and the software includes a web-based console for easy configuration and monitoring. However, new users might face a learning curve due to the complexity of the network and its features.
### Security
Security is at the core of I2P's design. The network employs multiple layers of encryption and routing to protect user data. Regular updates and community audits ensure that the software remains secure against emerging threats.
### Limitations
Despite its strengths, I2P has some limitations. The network can experience latency issues due to the multiple layers of encryption and routing. Additionally, the relatively small user base compared to other anonymity networks like Tor can impact the overall speed and availability of services.
### Conclusion
I2P is a powerful tool for anyone seeking to enhance their online privacy and security. Its robust architecture, combined with a wide range of supported applications, makes it a versatile choice for both casual users and privacy enthusiasts. While it may require some initial effort to fully understand and utilize its features, the benefits of using I2P far outweigh the challenges.
In a world where digital privacy is increasingly under threat, I2P stands out as a beacon of hope, providing a secure and anonymous communication platform for all.
The Invisible Internet Project, commonly known as I2P, is a robust and sophisticated software solution developed by the I2P Team. It is designed to provide users with a secure and anonymous communication network, ensuring privacy and freedom from surveillance.
### Overview
I2P is an open-source project that focuses on creating a decentralized and anonymous overlay network. This network allows applications to send messages to each other securely and anonymously. Unlike traditional internet protocols, I2P is built to operate within its own network, providing a layer of privacy that is difficult to penetrate.
### Key Features
1. **Anonymity**: I2P excels in providing anonymity for both the sender and receiver. It achieves this through a complex routing mechanism known as garlic routing, which encrypts multiple messages together to obfuscate the data.
2. **Decentralization**: The network is decentralized, meaning there is no central authority or server that can be targeted for attacks. This makes I2P highly resilient against censorship and surveillance.
3. **Versatile Applications**: I2P supports a wide range of applications including web browsing, email, file sharing, and instant messaging. It is compatible with various protocols and can be integrated with existing applications to enhance their privacy features.
4. **End-to-End Encryption**: All communications within the I2P network are end-to-end encrypted, ensuring that data remains confidential and tamper-proof during transit.
5. **Community-Driven**: Being an open-source project, I2P benefits from a vibrant community of developers and users who continuously contribute to its improvement and security.
### Performance
I2P is designed to be efficient and scalable. It can handle a large number of users and high traffic volumes without significant degradation in performance. The software is lightweight and can run on various operating systems including Windows, macOS, Linux, and Android.
### Usability
While I2P offers advanced privacy features, it is also user-friendly. The installation process is straightforward, and the software includes a web-based console for easy configuration and monitoring. However, new users might face a learning curve due to the complexity of the network and its features.
### Security
Security is at the core of I2P's design. The network employs multiple layers of encryption and routing to protect user data. Regular updates and community audits ensure that the software remains secure against emerging threats.
### Limitations
Despite its strengths, I2P has some limitations. The network can experience latency issues due to the multiple layers of encryption and routing. Additionally, the relatively small user base compared to other anonymity networks like Tor can impact the overall speed and availability of services.
### Conclusion
I2P is a powerful tool for anyone seeking to enhance their online privacy and security. Its robust architecture, combined with a wide range of supported applications, makes it a versatile choice for both casual users and privacy enthusiasts. While it may require some initial effort to fully understand and utilize its features, the benefits of using I2P far outweigh the challenges.
In a world where digital privacy is increasingly under threat, I2P stands out as a beacon of hope, providing a secure and anonymous communication platform for all.
OS: Windows 11, Windows 10 32/64 bit, Windows 8 32/64 bit, Windows 7 32/64 bit
Add Your Review or 64-bit Compatibility Report
Top Other 64-bit downloads
Adobe Flash Player 10 for 64-bit Windows Preview 2
Enables native 64-bit support on Linux operating systems
Freeware
TeamViewer Portable 15.74.5
Effortlessly connect and control devices remotely with TeamViewer Portable.
Freeware | $32.90
Portable iReasoning MIB Browser Enterprise 14.0 B4717
A powerful and easy-to-use tool powered by iReasoning SNMP API
Trialware | $595.00
nWOL 2.1.91
nWOL: Efficiently manage Wake-on-LAN for remote device access.
Freeware
tags: nWOL, download nWOL, nWOL free download, Wake on LAN, Scan Host, MAC Address, WoL, WakeOnLAN, Host, MAC
Google Apps Manager 7.33.03

Manage Google Workspace accounts and services effortlessly with GAM.
Open Source
Thunderbird Portable 115.12.1
Redesigned version of Thunderbird that you can take with you
Open Source
RouterOS 7.21.2 Stable
Powerful routing software for advanced network management and control.
Demo | $45.00
Members area
Top 64-bit Downloads
-
Internet Explorer 8 for
Windows Vista 64-bit and
Windows Server 2008
64-bit
x64 freeware download -
Adobe Flash Player 10
for 64-bit Windows Preview 2
x64 freeware download -
SSuite NetSurfer Extreme
x64 1.8.14.14
x64 freeware download -
Google Chrome x64 bit 126.0.6478.127
x64 freeware download -
SoftPerfect Bandwidth
Manager 3.3.0
x64 shareware download -
Xlight FTP Server
Standart x64 3.9.4.2
x64 trialware download -
Radio Downloader 64-bit 0.32
x64 open source download -
SSuite NetSurfer Browser
x64 2.30.16.8
x64 freeware download -
HTTPNetworkSniffer
64-bit 1.63
x64 freeware download -
DameWare Mini Remote
Control 64bit 12.3.0.12
x64 trialware download
Top Downloads
-
Internet Explorer 8 for
Windows Vista 64-bit and
Windows Server 2008
64-bit
freeware download -
Adobe Flash Player 10
for 64-bit Windows Preview 2
freeware download -
TeamViewer Host 15.74.5
freeware download -
Teleparty (formerly
Netflix Party) 5.5.6
trialware download -
Google Chrome 145.0.7632.46
freeware download -
BrowseEmAll 9.7.0
trialware download -
uTorrent (µTorrent) 3.6.0 B47124
open source download -
Gtraffic bot 2.0.8
shareware download -
LanguageTool for Chrome 10.0.12
shareware download -
Toggl Track for Firefox 4.11.8
shareware download -
RegExp Download
Organizer 0.5.2
open source download -
X-Browser 1.4
freeware download -
Yandex Browser 24.6.1.766
freeware download -
SSuite NetSurfer Extreme
x64 1.8.14.14
freeware download -
BitComet 2.20
freeware download